A new bit of Mac malware has been discovered in the wild. Bitdefender Labs has found a new piece of work, which it has named “Backdoor.MAC.Elanor.” The app is currently available on a number of reputable download sites such as MacUpdate.
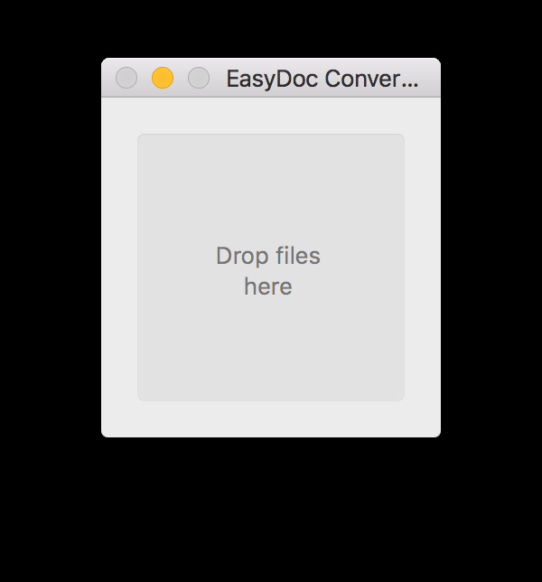
Bitdefender Labs, via 9to5Mac:
The backdoor is embedded into a fake file converter application that is accessible online on reputable sites offering Mac applications and software. The EasyDoc Converter.app poses as a drag-and-drop file converter, but has no real functionality – it simply downloads a malicious script.
This is a nasty backdoor that can steal data, execute remote code and access the webcam, among other things …
MacUpdate has reportedly been advised of the existence of the malware on its site, but at the time of this article, it has not been removed from the site.
Bitdefender’s technical lead Tiberius Axinte says Backdoor.MAC.Elanor is a nasty bit of code, and there is basically no limit to the havoc it could possible cause on your machine.
“This type of malware is particularly dangerous as it’s hard to detect and offers the attacker full control of the compromised system,” says Axinte. “For instance, someone can lock you out of your laptop, threaten to blackmail you to restore your private files or transform your laptop into a botnet to attack other devices. The possibilities are endless.”
The app is not signed by an Apple Developer ID, so make sure you have your Mac set to open only apps from the Mac App Store, or known developers, that will keep the app from opening. It goes without saying that users should always be careful when downloading apps from websites, even reputable ones.
A full report on the malware can be found here. 9to5Mac reports Bitdefender will offer up more details about the malware later this morning. When we find out more, we’ll report it right here.


