New ransomware has been found in the wild that targets macOS software pirates. The “poorly coded” malware, created in Swift, promises to crack the copy protection on popular software suites, such as Microsoft Office and Adobe products and instead encrypts the user’s files and demands payment. However, there is no way to decrypt the files, even if the victim pays the ransom.
Circulating via BitTorrent sites and called “Patcher,” the malware poses as a crack for pirates to get around copy protection and licensing systems used in popular software suites. Researcher Marc-Etienne M.Léveillé found two different fake patchers that used the same code, posing as ways to unlock Microsoft Office for Mac 2016 and Adobe Premiere Pro CC 2017, but suggests there may be more instances of the malware circulating around under different names.
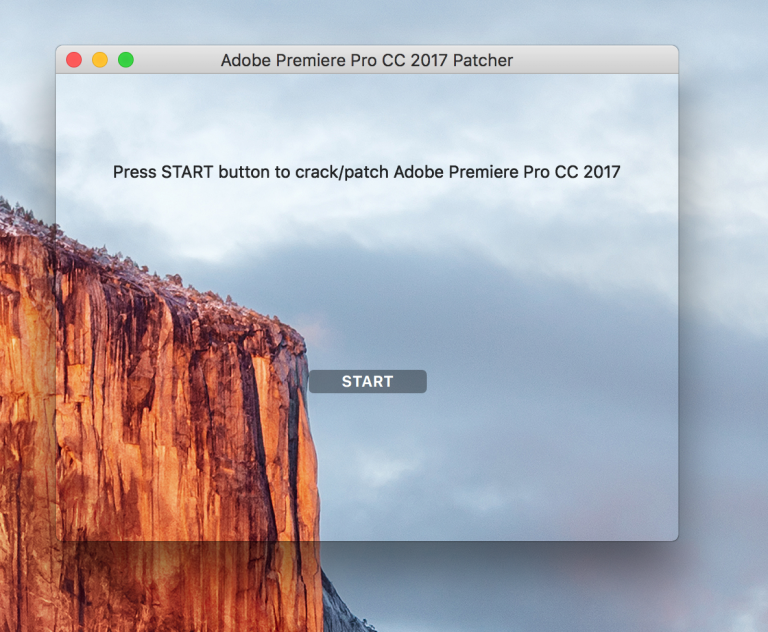
When executed, the malware opens a window telling them to press the Start button to patch their pirated software. When the button is clicked, the ransomware places a “readme” file in various user directories, and then encrypts all other user files via a randomly generated 25-character key in an archive, and deletes the original files.
The Readme file explains to the user the files are encrypted, and to pay 0.25 bitcoin to a specific wallet address to unlock them within seven days. While it is claimed files will be decrypted within 24 hours of the random’s payment, another option to pay 0.45 bitcoin is also offered, touting decryption within ten minutes.
“Patcher” is just the latest in a rash of recent malware strains targeting the macOS operating system and its users. In the last 30 days or so, malware posing as both an Adobe Flash Player update and a Microsoft Word macro have been found, targeted at the U.S. defense industry and various human rights groups. An Xagent malware package reportedly created by Russian hackers has also been discovered.
No Way to Decrypt Files, Even if Ransom is Paid
All victims are presented with the same Bitcoin wallet and email address, instead of information unique to each infection. So far, it appears no one has paid the ransom, as there are no transactions in that specific Bitcoin wallet.
Even if a victim does pay the ransom, there is no way to get their files back, as there is no code in the Malware, “poorly coded” in Swift, to send the key to the user to decrypt the files. Léveillé recommends users keep a current offline backup of all important data, as well as security software, to help protect threats such as this.


