Apple’s new Mac operating system, macOS High Sierra, shipped with a vulnerability that allows apps to steal Keychain passwords in plaintext. Thankfully, it requires users to intentionally override macOS’s built-in security.
on High Sierra (unsigned) apps can programmatically dump & exfil keychain (w/ your plaintext passwords)🍎🙈😭 vid: https://t.co/36M2TcLUAn #smh pic.twitter.com/pqtpjZsSnq
— Patrick Wardle (@patrickwardle) September 25, 2017
Synack research director, Patrick Wardle, was able to use the security hole to grab login information for a number of websites, including logins for Facebook and Bank of America. Wardle told Forbes the exploit doesn’t require root access, and works as long as the user is logged in.
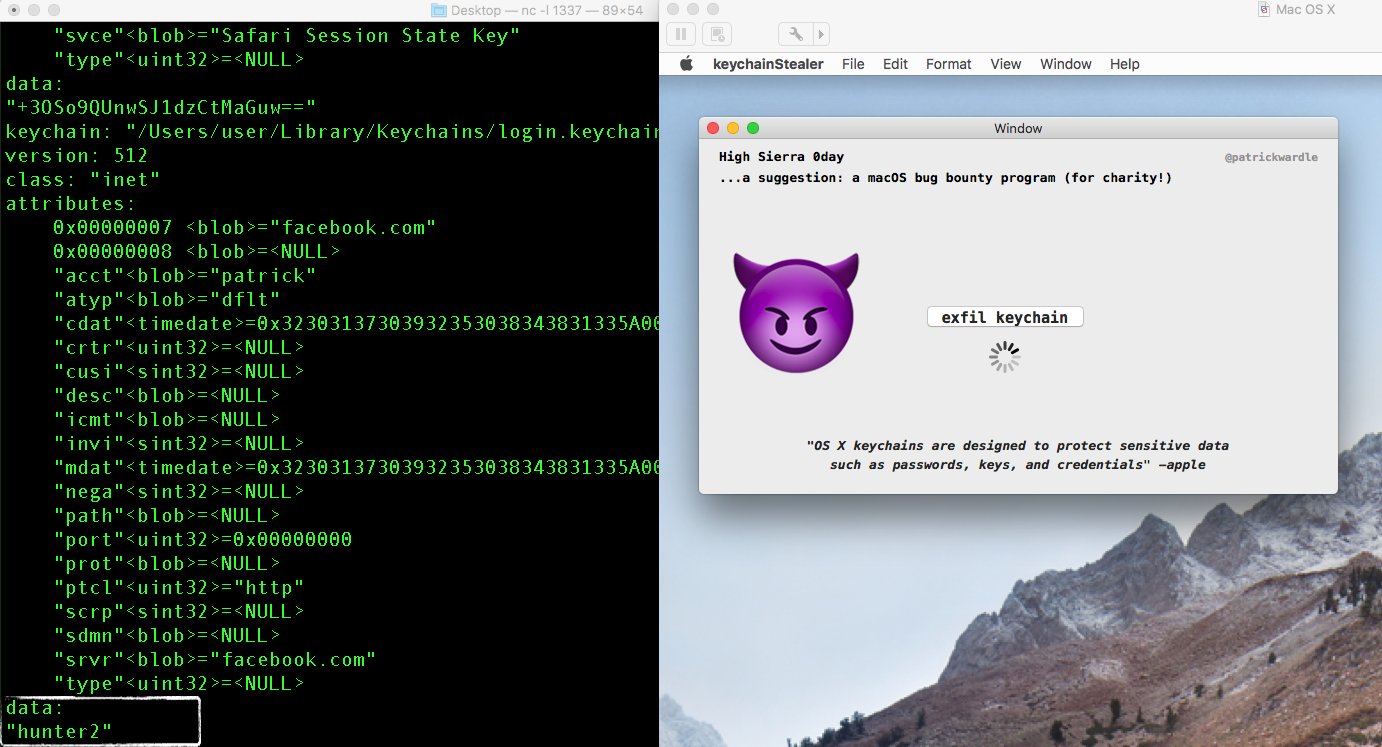
The vulnerability does require that users download, install and run a malicious app by deliberately overriding macOS security settings, which would include a warning about trusting unsigned software.
Wardle says other versions of macOS are also vulnerable to the exploit.
other versions of macOS are vulnerable too ☠️😡 Not sure what🍎 is thinking 😭😭😭
— Patrick Wardle (@patrickwardle) September 25, 2017
macOS High Sierra was released to the public on Monday, following a lengthy beta testing period. It isn’t clear whether Apple knew of the vulnerability, or if it is working on a fix.


