A warning has been issued by European security researcher Sebastian Schinzel warning of critical vulnerabilities in PGP/GPG and S/MIME email encryption software that could reveal the plaintext of encrypted emails. Previously sent mails could also be exposed.
The vulnerabilities affect Apple Mail, Mozilla Thunderbird with Enigmail and Microsoft Outlook with GPG4win.
We'll publish critical vulnerabilities in PGP/GPG and S/MIME email encryption on 2018-05-15 07:00 UTC. They might reveal the plaintext of encrypted emails, including encrypted emails sent in the past. #efail 1/4
— Sebastian Schinzel @seecurity@infosec.exchange (@seecurity) May 14, 2018
Schinzel tweeted about the flaw late Sunday night, via his Twitter account. A full research paper on the flaw was published on early Monday morning. The paper provides a full description of the vulnerabilities. There are currently no fixes available for the flaw.
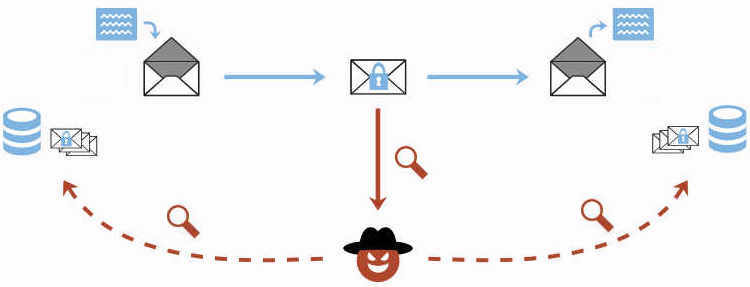
The EFAIL attacks exploit vulnerabilities in the OpenPGP and S/MIME standards to reveal the plaintext of encrypted emails. In a nutshell, EFAIL abuses active content of HTML emails, for example externally loaded images or styles, to exfiltrate plaintext through requested URLs. To create these exfiltration channels, the attacker first needs access to the encrypted emails, for example, by eavesdropping on network traffic, compromising email accounts, email servers, backup systems or client computers. The emails could even have been collected years ago.
The attacker changes an encrypted email in a particular way and sends this changed encrypted email to the victim. The victim’s email client decrypts the email and loads any external content, thus exfiltrating the plaintext to the attacker.
Users of PGP/GPG and S/MIME are being told to immediately disable or uninstall PGP_decryption tools and seek other ways, such as Signal, to send and receive sensitive encrypted information.
For detailed information about the vulnerabilities, visit the EFAIL website.