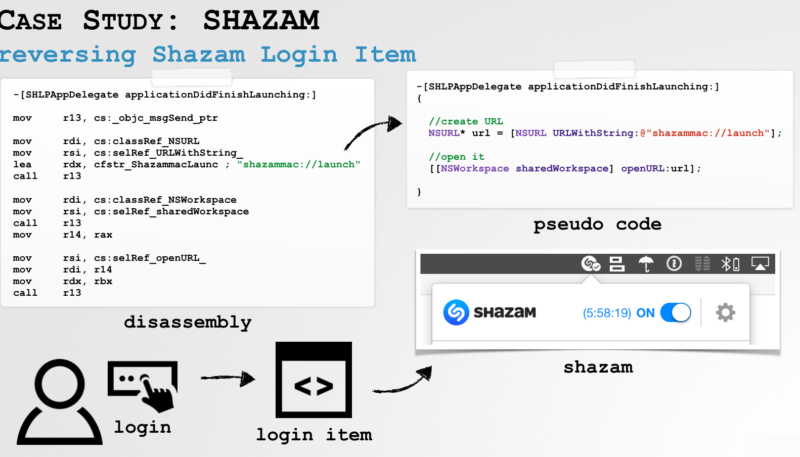
Security researcher Patrick Wardle has demoed an exploit found in macOS that allows malware to be remotely installed an a Mac via the use of custom URL handlers in Safari.
The WINDSHIFT APT deals largely with “Do you want to allow” popups familiar to any macOS user, explains security researcher Patrick Wardle. These document handlers are frequently seen in use when clicking on an App Store link or PDF, which asks users for permission before opening the link or file in a registered app like the Mac App Store or Preview.
The exploit uses document handlers, which are used by an application to notify macOS to let it know the type of documents they can handle. For example, Preview advertises the ability to handle various file types.
While it is beyond this article to offer a full in-depth explanation of how the exploit works, Wardle’s blog post offers an excellent explanation of the exploit.