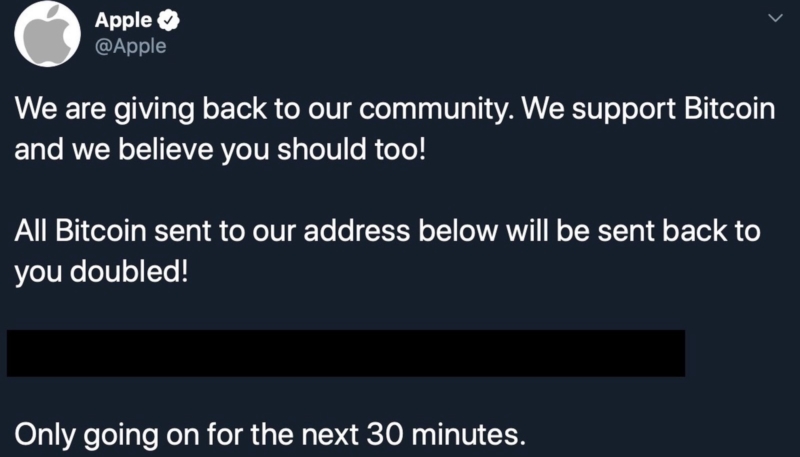
Twitter has posted another update on the Bitcoin-related security breach it suffered two weeks ago, which saw the Twitter accounts of Apple and other verified high-profile companies and individuals hacked by Bitcoin scammers.
The social network says a small number of employees were targeted in a “phone spear-phishing attack,” that exploited human vulnerabilities to mislead certain employees to provide access to Twitter’s internal systems.
The attack on July 15, 2020, targeted a small number of employees through a phone spear phishing attack. This attack relied on a significant and concerted attempt to mislead certain employees and exploit human vulnerabilities to gain access to our internal systems.
Hackers used internal Twitter tools to target 130 accounts and 45 of those accounts saw hackers initiate a password reset, providing full access to the accounts to send tweets.
Affected accounts included those held by Apple, Tesla CEO Elon Musk, Amazon CEO Jeff Bezos, Microsoft CEO Bill Gates, former U.S. President Barack Obama, presidential candidate Joe Biden, and others.
In the wake of the attack, Twitter temporarily locked some users’ accounts and limited features on others. Most of the features have been restored, but some are still not working properly.
Twitter says it is accelerating several of their pre-existing security workstreams and improvements to their tools.
We’re always investing in increased security protocols, techniques and mechanisms – it’s how we work to stay ahead of threats as they evolve. Going forward, we’re accelerating several of our pre-existing security workstreams and improvements to our tools. We are also improving our methods for detecting and preventing inappropriate access to our internal systems and prioritizing security work across many of our teams. We will continue to organize ongoing company-wide phishing exercises throughout the year.