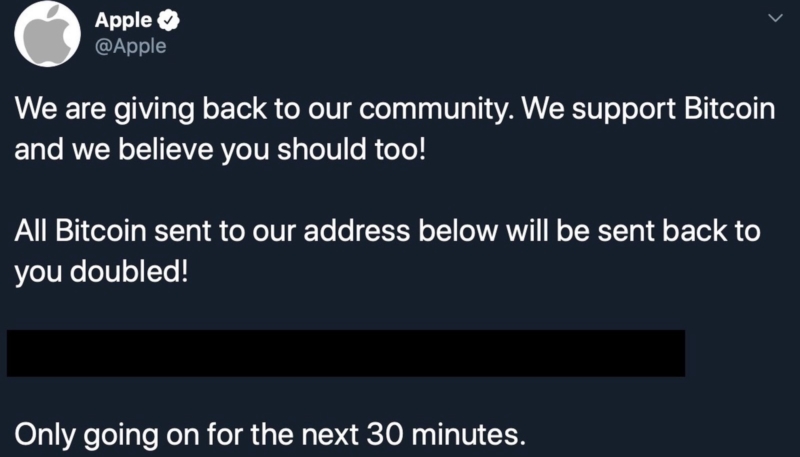
Several verified high-profile Twitter accounts were hacked on Wednesday in a cryptocurrency hack that earned hackers over $100,000 in the space of just a few hours. Twitter accounts hacked include those held by Apple, Tesla CEO Elon Musk, Amazon CEO Jeff Bezos, Microsoft CEO Bill Gates, and more.
Information is beginning to be revealed about the hack and how it happened. Twitter says it doesn’t believe any passwords were stolen in the hack, forcing the social network to temporarily lock all verified accounts. Now, a new report suggests that the hackers had help from the inside.
It appears that at least one Twitter employee and possibly more were involved in the takeover. Motherboard spoke to two of the alleged hackers, who claim they paid a Twitter employee to gain access to the hacked accounts using an internal tool. The tool is said to allow internal staff to change the emails associated with Twitter accounts, and it was this “feature” that allowed the security breach to take place.
Hackers used the compromised accounts to post tweets saying that if followers sent $1,000 Bitcoin to a certain wallet address then they would receive double the amount in return. Many users fell for the scam, earning the hackers over $100,000 in the space of two hours.
Twitter disclosed on Thursday that a social engineering attack targeted some of its staff as part of the hack attack.
We detected what we believe to be a coordinated social engineering attack by people who successfully targeted some of our employees with access to internal systems and tools.
— Support (@Support) July 16, 2020
The official Twitter Support account says it doesn’t believe passwords were compromised, and that accounts were locked as a purely precautionary move:
We have no evidence that attackers accessed passwords. Currently, we don’t believe resetting your password is necessary.
Out of an abundance of caution, and as part of our incident response yesterday to protect people’s security, we took the step to lock any accounts that had attempted to change the account’s password during the past 30 days […]
If your account was locked, this does not necessarily mean we have evidence that the account was compromised or accessed. So far, we believe only a small subset of these locked accounts were compromised, but are still investigating and will inform those who were affected.
We’re working to help people regain access to their accounts ASAP if they were proactively locked. This may take additional time since we’re taking extra steps to confirm that we’re granting access to the rightful owner.
Twitter says it believes approximately 130 accounts were targeted as part of the hack, but it hasn’t so far been able to confirm whether DMs were compromised. The FBI is also conducting an investigation.
The New York Times reports President Donald Trump’s Twitter account was not hacked due to additional safeguards that are in place to protect his account.
President Trump’s account was not affected by the breach, Kayleigh McEnany, the White House press secretary, said on Thursday. Mr. Trump’s account got extra protection after past incidents, according to a senior administration official and a Twitter employee, who would speak only anonymously because the security measures were private.
Security journalist Brian Krebs has identified a potential suspect:
Twitter account @shinji was tweeting out screenshots of Twitter’s internal tools […] Cached copies of @Shinji’s tweets prior to Wednesday’s attack on Twitter are available here and here from the Internet Archive. Those caches show Shinji claims ownership of two OG accounts on Instagram — “j0e” and “dead.”
KrebsOnSecurity heard from a source who works in security at one of the largest U.S.-based mobile carriers, who said the “j0e” and “dead” Instagram accounts are tied to a notorious SIM swapper who goes by the nickname “PlugWalkJoe.” Investigators have been tracking PlugWalkJoe because he is thought to have been involved in multiple SIM swapping attacks over the years that preceded high-dollar bitcoin heists […]
The profile image in the other Archive.org index of the @shinji Twitter account […] is the same image as the one included in the @Shinji screenshot above from Wednesday in which Joseph/@Shinji was tweeting out pictures of Twitter’s internal tools.
This individual, the source said, was a key participant in a group of SIM swappers that adopted the nickname “ChucklingSquad,” and was thought to be behind the hijacking of Twitter CEO Jack Dorsey‘s Twitter account last year.
The mobile industry security source told KrebsOnSecurity that PlugWalkJoe in real life is a 21-year-old from Liverpool, UK. [Krebs names the suspect, but we have not done so here to avoid compromising any legal proceedings which may follow.]
The source said PlugWalkJoe is in Spain where he was attending a university until earlier this year. He added that PlugWalkJoe has been unable to return home on account of travel restrictions due to the COVID-19 pandemic […]
PlugWalkJoe was the subject of an investigation in which a female investigator was hired to strike up a conversation with PlugWalkJoe and convince him to agree to a video chat. The source further explained that a video which they recorded of that chat showed a distinctive swimming pool in the background.
According to that same source, the pool pictured on PlugWalkJoe’s Instagram account (instagram.com/j0e) is the same one they saw in their video chat with him.
We’ll keep you posted as we learn more.
(Some information via 9to5Mac)