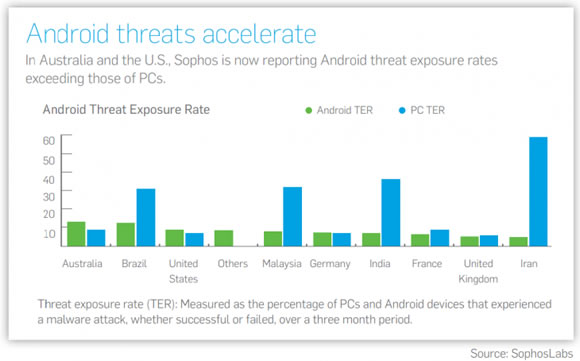
Sophos has released its Security Threat Report 2013. The report shows that malware writers have adjusted to the new diversity of platforms by targeting such operating systems as Android, and yes, OS X.
Sophos called Android “today’s biggest target” and went over a few examples. The security firm noted that currently the most common business model for Android malware attacks is to install fake apps that secretly send expensive messages to premium rate SMS services.
This goes along with what McAfee found. Android.FakeInstaller, also known as OpFake, which generates revenue by silently sending expensive text messages in the background, makes up more than 60 percent of Android samples the company sees.
As for the OS X world, Sophos stated, “More users, emerging risks.” Even though OS X has nowhere near the installed user base of Windows or Android, its has an ever growing user base, so threats for it are also growing.
One malware threat, well covered in the press, was the Flashback threat. The malware infected hundreds of thousands of Apple computers back in April. By April 2012, Flashback was installing itself as a drive-by download, exploiting an unpatched Java vulnerability on OS X.
 Sophos says Mac malware is evolving at a rapid pace. As its sophistication improves, it becomes ever more dangerous. As such, the malware threat for OS X is ever growing.
Sophos says Mac malware is evolving at a rapid pace. As its sophistication improves, it becomes ever more dangerous. As such, the malware threat for OS X is ever growing.
OS X, originally built on BSD UNIX, has a stronger security model than some other platforms. It is still vulnerable to threats such as Flashback via the unpatched vulnerabilities.
Sophos suggests ways for IT professionals to protect machines running OS X from malware threats.
1) User education – Work with users, make them aware of the security threats that do exist in the Mac computing world.
2) Layered protection – Constantly updated Mac endpoint protection is now essential— but so is protection for servers, mail and web gateways, and network infrastructure.
3) Mac-specific expertise – Either hire Mac specialists or train existing staff on the platform’s unique characteristics.
4) Strong IT processes and policies – Wherever possible, extend ITIL-type best practice policies to Macs as well as PCs. Provide for rapid and automated patching of Macs as well as Windows devices. And, of course, patch Java, Flash, and applications as well as OS X itself.
5) Realism – Since Macs are often used by senior executives and creative teams who need maximum control over their computers, you may need to accept that some Macs will be untrusted. But untrusted should not mean unprotected. You should still offer users whatever protection is practical.
Sophos also included a glimpse of what they say are “things to come” in their report. The company expects the increased availability of malware testing platforms will make it easier for malware to slip through traditional business security systems. It also mentions that with the increased integration of GPS and NFC into mobile platforms, it is highly advisable to be watchful for attacks built upon those technologies.